Official Trezor™ Login — Desktop & Web App for Hardware Wallets
Trezor Login: A Complete Guide to Secure Access


When it comes to cryptocurrency security, the concept of “login” is very different from traditional online accounts. With Trezor, you don’t log in using a username and password stored on a server. Instead, authentication happens through your hardware wallet. The login process is designed to protect private keys and ensure that only the physical device holder can access the wallet.
Developed by SatoshiLabs, Trezor devices use a hardware-based authentication system that eliminates many of the vulnerabilities associated with standard login systems. This article explains how Trezor login works, how to access your wallet securely, and best practices for protecting your crypto assets.
What Does “Trezor Login” Mean?
Unlike exchanges or web wallets, Trezor does not require you to create an online account. There is no email registration, no password stored in a database, and no centralized login server.
Instead, logging in means:
- Connecting your Trezor device
- Entering your PIN
- Optionally entering your passphrase
- Accessing your wallet through Trezor Suite
Your device itself acts as the authentication key. Without physical access to it—and without knowing the PIN—no one can access your wallet.
How to Log In to Trezor Suite
Step 1: Connect Your Device
Plug your Trezor into your computer using the USB cable. You can access your wallet via the Trezor Suite desktop application, which is the recommended method for maximum security.
Trezor Suite will automatically detect your device once connected.
Step 2: Enter Your PIN


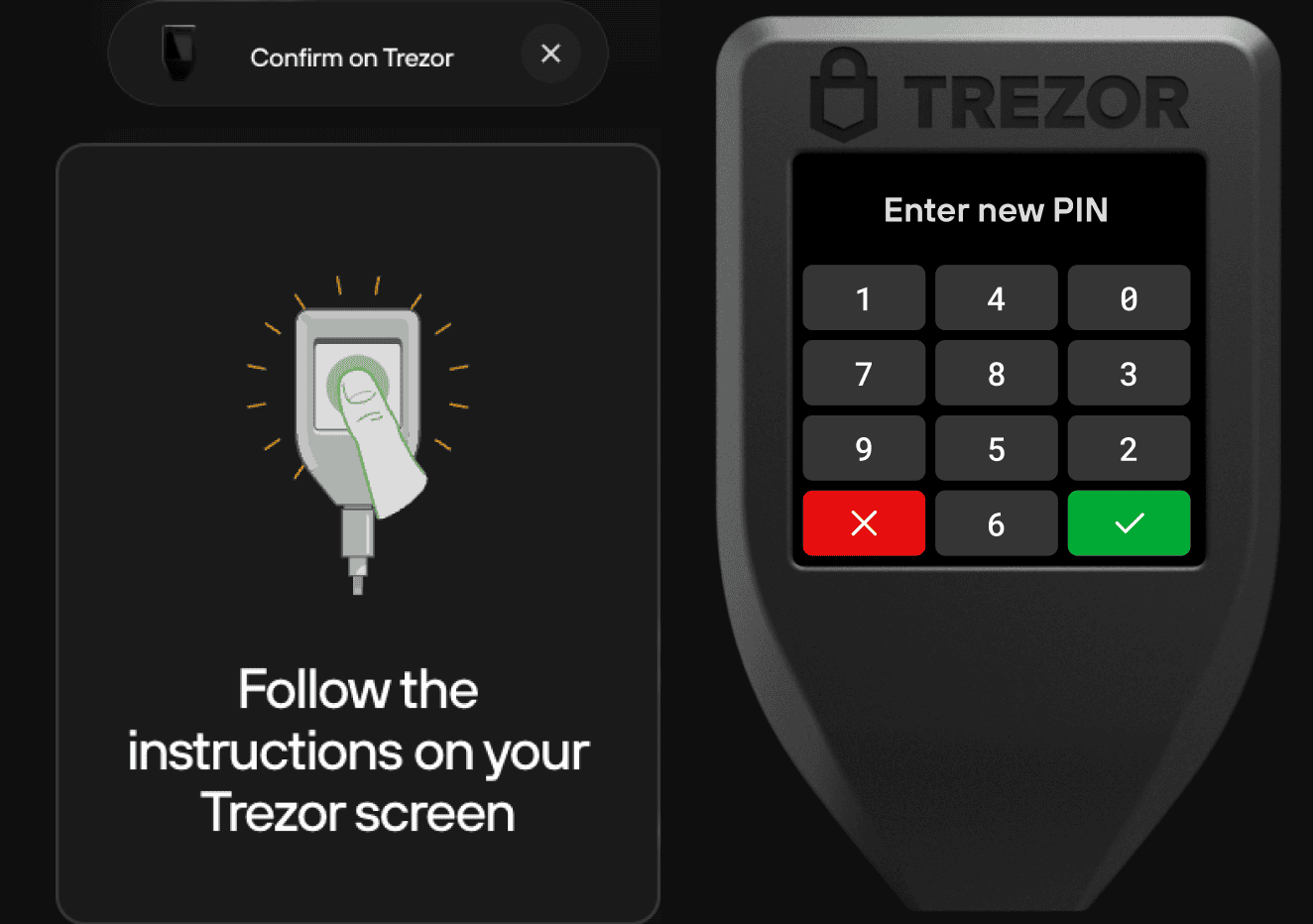

When prompted, you must enter your PIN. The PIN system is designed to prevent keylogging attacks. Instead of typing numbers normally, you enter the PIN according to a scrambled layout displayed on your device screen.
- On the Trezor Model One, the PIN is entered using a matrix displayed on the device.
- On the Trezor Model T, the PIN can be entered directly on the touchscreen.
This prevents malware on your computer from capturing your PIN.
Step 3: Enter Passphrase (Optional)
If you enabled passphrase protection, you must enter your custom passphrase after the PIN.
The passphrase creates a hidden wallet. Without it, the hidden account cannot be accessed—even if someone has your device and recovery seed.
This feature provides an advanced layer of security for users storing significant cryptocurrency holdings.
Step 4: Access Your Wallet Dashboard
Once authenticated, Trezor Suite displays your portfolio dashboard. From here, you can:
- View balances
- Send and receive cryptocurrency
- Manage multiple accounts
- Adjust security settings
Every transaction still requires confirmation directly on the device screen.
How Trezor Login Enhances Security
Trezor login differs from traditional authentication systems in several important ways:
1. No Centralized Password Storage
There is no server storing your login credentials. This eliminates risks such as database breaches or password leaks.
2. Physical Confirmation Required
Transactions must be physically approved on the device. Even if your computer is compromised, attackers cannot send funds without your confirmation.
3. Protection Against Phishing
Because Trezor login requires hardware interaction, phishing websites cannot access your wallet without your device and PIN.
4. Brute-Force Protection
If someone attempts to guess your PIN repeatedly, the device automatically increases the delay between attempts. This makes brute-force attacks impractical.
What Happens If You Forget Your PIN?
If you forget your PIN but still have your recovery seed, you can reset the device and restore your wallet.
The recovery seed is a 12- or 24-word phrase generated during initial setup. It is the master backup of your wallet.
Important:
- Never store your seed digitally.
- Never share it.
- Never enter it on suspicious websites.
If both your device and recovery seed are lost, your funds cannot be recovered.
Using Trezor for Website Authentication
In addition to wallet access, Trezor devices can also function as hardware authentication tools for supported websites. This means you can log in to certain services using your Trezor as a cryptographic identity key.
This feature adds another layer of protection compared to traditional passwords and even two-factor authentication methods.
Common Login Mistakes to Avoid
Even with strong hardware protection, user mistakes can compromise security. Here are some common issues:
- Entering recovery seed words on a fake website
- Falling for phishing emails claiming “wallet issues”
- Using unofficial wallet software
- Leaving your device unattended while connected
Always verify that you are using official Trezor software and double-check URLs before interacting with your wallet.
Why Trezor Login Is More Secure Than Exchange Accounts
When you log into a centralized exchange, your funds are stored on company servers. Even with strong passwords and two-factor authentication, your assets are still under third-party control.
With Trezor login:
- You control the private keys
- Authentication requires physical device access
- No centralized entity holds your funds
This aligns with the crypto principle: “Not your keys, not your coins.”
Additional Security Tips
To maximize login security:
- Use a strong and unique PIN
- Enable passphrase protection
- Keep your firmware updated
- Store your recovery seed securely offline
- Use the desktop version of Trezor Suite
Taking these steps ensures that your login process remains secure long-term.
Who Benefits Most from Trezor Login?
Trezor login is ideal for:
- Long-term cryptocurrency investors
- Security-conscious individuals
- Users holding large crypto balances
- Anyone seeking self-custody solutions
If you prioritize privacy and full asset control, hardware-based login offers significant advantages over standard online authentication systems.
Final Thoughts
Trezor login represents a fundamental shift away from traditional username-password systems. Instead of trusting centralized servers, authentication is handled by a secure hardware device in your possession.
By combining PIN protection, optional passphrases, and physical transaction confirmation, Trezor creates a powerful barrier against hacking, phishing, and unauthorized access.
In a digital landscape where cyber threats continue to evolve, relying on hardware-based authentication provides peace of mind. With Trezor Suite and your Trezor device working together, login becomes not just a routine step—but a robust security feature designed to protect your financial sovereignty.